ON THIS PAGE:
Overview
In the Server module, several objects can be secured at the object level.
Default object security provides the Everyone role with implicit view privileges for all objects in the system. When securing a Server object, you will need to remove the View privilege from the resource, as well as default object privileges for other roles.
When applying object-level privileges, it is important to remember the cascading nature of privileges applied at the resource-level. If a role has explicit View privileges (or higher) on the resource, all users with that role can view all objects for that resource.
If you intend on changing security for specific objects, such as hierarchies, avoid explicitly setting privileges on the relevant resource in Server Management.
Changing object-level security for individual objects is done directly within the relevant configuration section Server Management, and requires Server administrator privileges.
What the Privileges Mean
Each resource may have different privileges. This is a list of the privileges for each resource, and what they mean.
Calculations
These privileges apply to calculation tags.
| Privilege | What it means |
| View | See the calculation tag in Server Management and Explorer. |
| Edit | Modify the calculation tag in Server Management. |
| Delete | Delete the calculation tag from Server Management. |
Datasources
These privileges apply to the datasource, and any tags or queries associated with the datasource.
| Privilege | What it means |
| View | See the datasource and associated tags or datasets, in both Server Management and Explorer. |
| Write | Write to the tags or datasets associated with a datasource, from Explorer. Note: The Write flag on the datasource must be enabled for this to take effect. If the flag is not enabled, this privilege will have no effect. |
| Edit | Modify the datasource and associated tags or datasets, in Server Management. |
| Delete | Modify the datasource and associated tags or datasets, from Server Management. |
Digital States
These privileges apply to digital states and digital state sets.
Note: Digital states cannot be individually secured, they can only be secured via Role Privileges.
| Privilege | What it means |
| View | All users are able to see all digital states, they cannot be individually secured. |
| Edit | Modify digital state sets and digital states, in Server Management. |
| Delete | Delete digital state sets and digital states, from Server Management. |
Entities
These privileges apply to entities.
| Privilege | What it means |
| View | See the entity in Server Management and Explorer. |
| Edit | Modify the entity in Server Management and Explorer. |
| Delete | Delete the entity in Server Management and Explorer. |
Hierarchies
These privileges apply to hierarchies.
| Privilege | What it means |
| View | See the hierarchy in Server Management and Explorer. |
| Edit | Modify the hierarchy in Server Management and Explorer. |
| Delete | Delete the hierarchy in Server Management and Explorer. |
Images
These privileges apply to images.
Note: Images cannot be individually secured, they can only be secured via Role Privileges.
| Privilege | What it means |
| View | All users are able to see all images, they cannot be individually secured. |
| Edit | Modify the image in Server Management and Explorer. |
| Delete | Delete the image from Server Management. |
Links
These privileges apply to links.
| Privilege | What it means |
| View | See the link and its link group, in Server Management and Explorer. |
| Edit | Modify the link and its link group, in Server Management. |
| Delete | Delete the link and its link group, from Server Management. |
Templates
These privileges apply to templates and their associated attributes.
| Privilege | What it means |
| View | See the template and associated attributes, in Server Management and Explorer. |
| Edit | Modify the template and associated attributes, in Server Management. |
| Delete | Delete the template and associated attributes, from Server Management. |
Units
These privileges apply to units.
Note: Units cannot be individually secured, they can only be secured via Role Privileges.
| Privilege | What it means |
| View | All users are able to see all units, they cannot be individually secured. |
| Edit | Modify the unit in Server Management. |
| Delete | Delete the unit from Server Management. |
Where the Privileges are Found
Select an option from the toolbar and follow the steps in the table below.
Note: Not all resources can be individually secured.
| Resource | Toolbar | Select the following: |
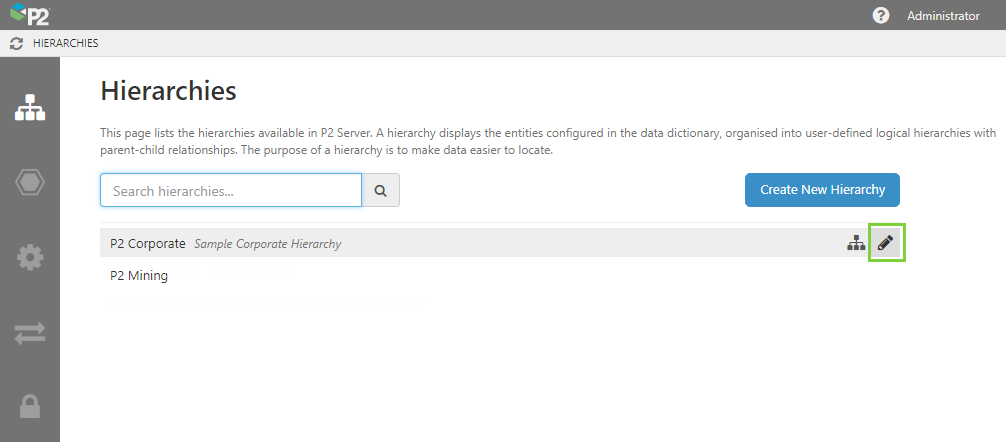
| Hierarchies |
Hierarchies
|
1. One of the hierarchies on the list 2. One of the locations on the list 3. Edit
Else, select Create New Hierarchy
|
| Entities |
Entities
|
1. One of the entities on the list 2. Edit (Details)
Else, select Create New Entity
|
|
Datasources |
Connections
|
1. Datasources
2. One of the datasources on the list Else, select Create New Datasource
|
|
Calculations |
Configuration
|
1. Calculations
2. One of the calculations on the list Else, select Create New Calculation
|
|
Links |
Configuration
|
1. Links
2. One of the links on the list Else, select Create New Link
|
|
Templates |
Configuration
|
1. Templates
2. One of the Templates on the list Else, select Create New Template
|
| Security |
Security
|
1. Privileges
2. One of the roles on the list |
| Forms |
Shift Log Admin
|
1. One of:
2. One of the forms on the list
3. Privileges are found under the expandable tab on the right side of the page
|
Tutorial 1. Changing Object Privileges
1. In Server Management, open the object for which you want to change the privileges. See Where the Privileges are Found.
We will use a hierarchy object as the example for this tutorial.
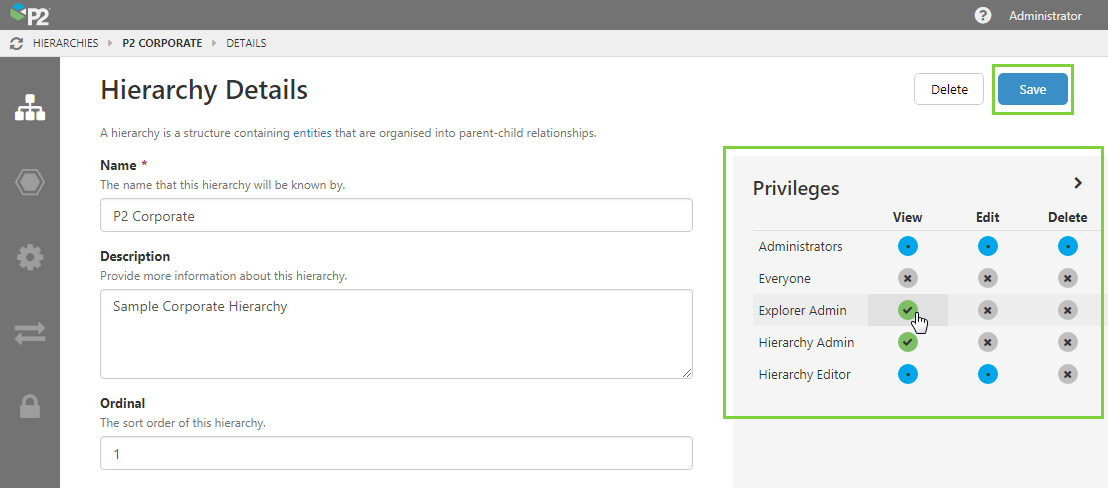
2. Click the Edit ![]() icon for the object (hierarchy) you want to edit.
icon for the object (hierarchy) you want to edit.
3. For each role, click the relevant privileges you want to assign.
- To remove a privilege and lock down the object, click the green tick icon. Remember that privileges cascade from higher to lower levels, so a role with edit privileges will also have View privileges.
- To grant a privilege, click the grey icon.
- Blue icons indicate an inherited Role Privilege, which you cannot change from here.
What the Colours Mean
The privileges matrix is colour-coded to indicate the cascading nature of privileges. The colours are:
![]() Grey: Privilege not granted
Grey: Privilege not granted
![]() Green tick: Privilege is explicitly granted, associated privileges will also be automatically granted.
Green tick: Privilege is explicitly granted, associated privileges will also be automatically granted.
![]() Green dot: Privilege is granted because a higher level privilege has been granted on the object.
Green dot: Privilege is granted because a higher level privilege has been granted on the object.
![]() Blue: Privilege is granted because it is inherited by a resource privilege.
Blue: Privilege is granted because it is inherited by a resource privilege.
4. When you have finished, click Save.













 Case Entry Forms
Case Entry Forms Log Entry Forms
Log Entry Forms General Entry Forms
General Entry Forms Summary Entry Forms
Summary Entry Forms